My Favorite Burp Suite Plugins

I thought I would share the few extensions I use in Burp Suite Pro. Keep in mind a couple of things here; 1) this list works for me and what is required of me professionally. Your mileage may vary depending on what environment you currently work in and what technologies. 2) there is no order to this list. Each plugin serves its own purpose equally to the others. In other words, don't take this as an "Absolute Top 10 Burp Suite Plugins 2021, please smash that like and subscribe button" post.
Active Scan++
by James Kettle
Active Scan++ is the #1 rated plugin on the BApp Store for a reason. The additional features it adds to the scanning engine in Burp Suite is good enough that it should just be integrated into the navtive application. Here is a small list of what AS++ adds:
- Potential host header attacks (password reset poisoning, cache poisoning, DNS rebinding)
- Edge side includes
- XML input handling
- Suspicious input transformation (eg 7*7 => '49', \x41\x41 => 'AA')
- Passive-scanner issues that only occur during fuzzing (install the 'Error Message Checks' extension for maximum effectiveness)
- Blind code injection via expression language, Ruby's open() and Perl's open()
- CVE-2014-6271/CVE-2014-6278 'shellshock' and CVE-2015-2080, CVE-2017-5638, CVE-2017-12629, CVE-2018-11776
- Provides insertion points for HTTP basic authentication.
While you can find this information out on your own, its very helpful to have these things automated as it can save you tons of time, especially when searching for low hanging fruit issues. Best of all, this doesn't require Burp Suite Pro && there is nothing you need to do extra. Start a normal scan like you normally would and the plugin will add in the extra checks for you. Ez pz
Software Vulnerability Scanner
by Vulners.com
Gonna be honest about this one. I don't like having to look up every single version number I come across to check for vulns. Sure, as time goes on you remember certain version numbers, but its pretty unrealstic to try to remember everything. Luckily, this extension exists. The features of this are:
- Detect vulnerable software by fingerprints or CPE
- Detect possible vulnerable paths which appeared in any exploits
How is this done? Depending on the options you have selected in the plugin, it will do this automatically as your crawl your way through a target site. It will discover version numbers of softwares running and automatically pull down what vulns exist for that particular build. Super handy and again, will save you loads of time!
Autorize
by Barak Tawily
You're gonna start to notice a pattern now. This is again another extension that will save you some time. Autorize works by you providing it with cookies (or not), generally of a lower privilege users while you crawl your way through your target site as a higher privileged user. As you do this, Autorize will resend every request with the cookie from the lower privileged user. If there are any successes, you will be notified of any authentication vulns.
I have used this before in conjunction with the above extensions to get an idea of things as I move around a target for the first time. Afterwards I will go back and review anything that looks interesting and give those findings adequate attention.
CSRF Scanner
by Adrian Hayter
I swear I actually test things, lol. This is yet another tool that is very useful in making your life a little easier. CSRF Scanner will passively scan for CSRF vulns while you do that magic that you do so well.
The only "downside" to this, is there are generally a lot of false positives. However, the more you use the tool and see the results, you are able to pick out what is legit and what is not just by looking. And like before, this lets you spend more time on actual findings.
Bypass WAF
by Josh Berry
If you've ever had to deal with a WAF before with a client you know how much of a pain that can be to deal with, especially if you've had to modify every single request in attempts to bypass said WAF.
Well fear no more! Bypass WAF does exactly what it says it does:
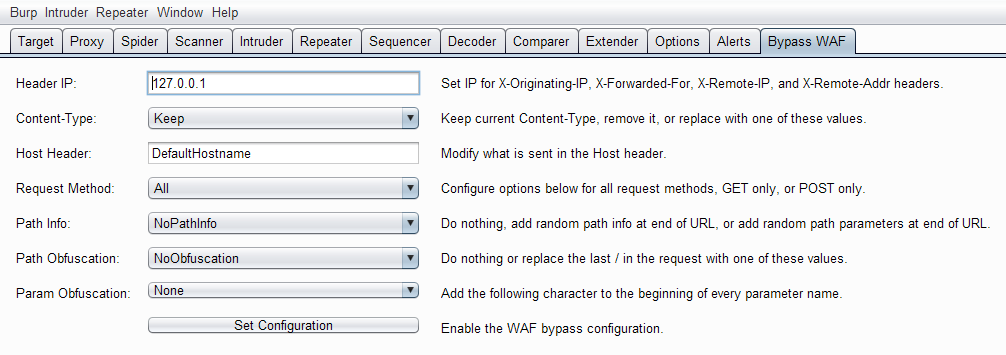
Using these options, you can fine tune the headers that the tool will automatically insert into each request, saving you tons of time and plenty of tears when you inevitably forget to Make-Every-Single-Hypen in these headers.
While these tools look like you're not really testing anything, that's actually where they are your best friend. Time is always against a pentester. You have finite about of it, so the more time you can dedicated to real issues vs. rabbit holes the better off you will be in the end and your client will be happier for it 👍🏼